HashiCorp Vault pipeline integration
Use secrets from Vault in Codefresh pipelines
Codefresh can use secrets from your HashiCorp Vault installation. This way you have full control over secret storage and rotation.
NOTE
This feature is for Enterprise accounts only.
Prerequisites
-
Up and running Vault instance
Codefresh supports HashiCorp Cloud Platform (HCP) Vault and self-managed Vault instances that run on the cloud, as well as behind the firewall (albeit with some differences in the authentication methods). -
Authentication method to use.
Codefresh supports the following methods:
| Method | Notes |
|---|---|
| Username/Password | Available for SaaS and Hybrid versions |
| Access Token | Available for SaaS and Hybrid versions |
| Kubernetes | Only available with Codefresh Runner installation |
| Google Cloud Engine | Only available with Codefresh Runner installation |
| App Role | Available for SaaS and hybrid version with Runner |
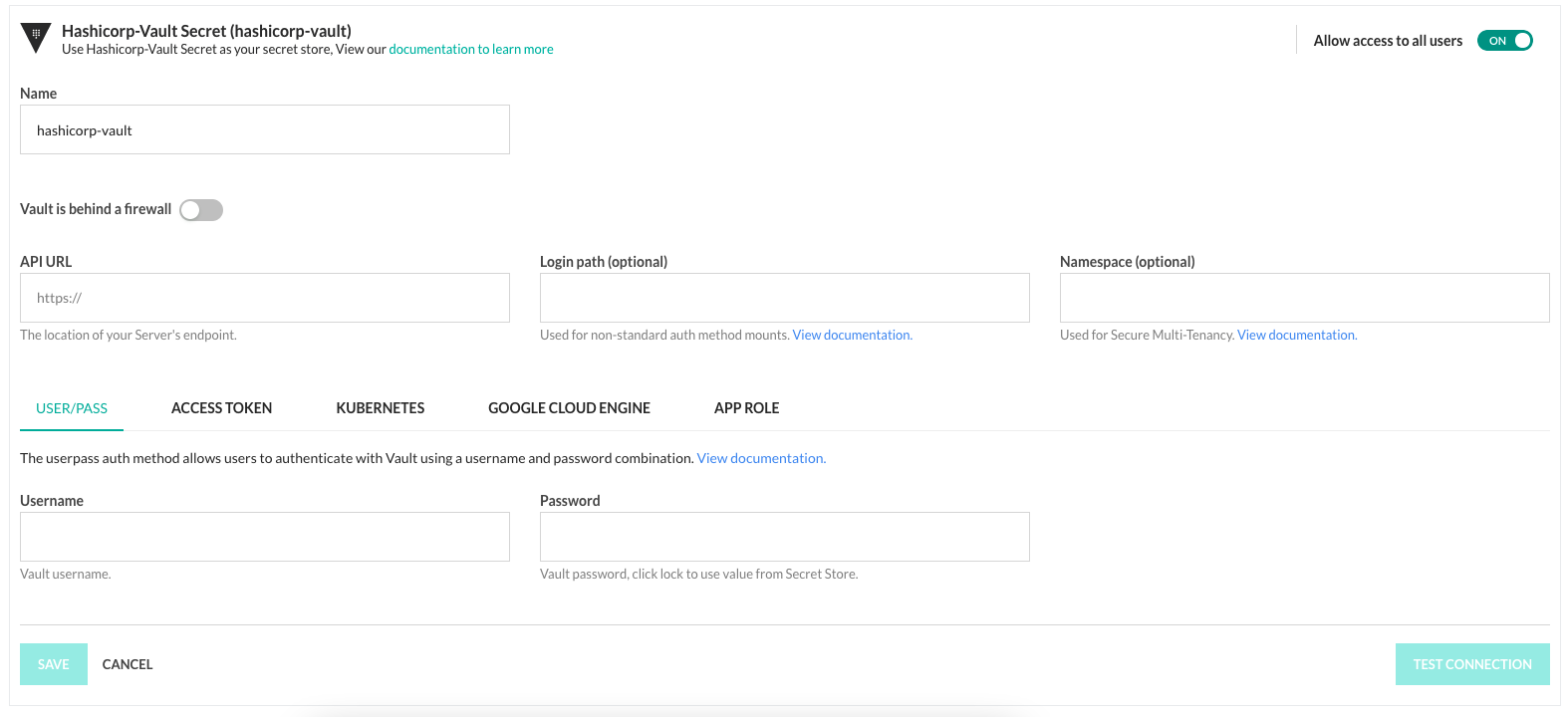
Set up HashiCorp Vault integration in the Codefresh UI
IMPORTANT
The name assigned to the integration must be unique within the account. Using the same name for other integrations or Shared Configuration contexts within pipelines will result in conflicts.
For troubleshooting, see Error: context already exists.
- In the Codefresh UI, on the toolbar, click the Settings icon, and then from the sidebar, select Pipeline Integrations.
- Select Secret Store and then click Configure.
- From the Add Provider dropdown, select Hashicorp vault.
- Do the following:
- Name: A unique name for the integration which is referenced in
codefresh.yaml. - If your Vault instance is behind a firewall, toggle Vault is behind a firewall to ON.
- To allow only Codefresh admins to change the Vault configuration, toggle Allow access to all users to OFF.
NOTE
The other settings are specific to your Vault authentication method. Refer to the Vault documentation on how to get the required values.
- Name: A unique name for the integration which is referenced in
- To apply the changes, click Save.
Set up HashiCorp Vault integration via Codefresh CLI
You can also create Vault integrations with the Codefresh CLI through the create context command.
The options available are identical to the UI settings.
For example, to create an integration with user/password authentication, you would run this command:
codefresh create context secret-store hashicorp-vault <my-integration> --sharing-policy AccountAdmins -app-url <http://vault.example.com> --username <my-user> --password <my-password>
<!— where:
-
is the name of the integration which is referenced in `codefresh.yaml`. -
is the name of the integration which is referenced in `codefresh.yaml`. -->
Using the HashiCorp Vault secret
To use the Vault secrets in pipelines, see secrets for pipelines.
Because a secret in Vault can contain multiple key-value pairs, you will need to put in the key name as well, according to the syntax {secrets.vault-store-name.path/to/secret@key}.
Related articles
Shared Configuration
Git integration for pipelines
Kubernetes integration for pipelines
Container registry integration for pipelines